Why do you need to manage your security risks?
While it’s true you’re very unlikely to be caught up in a terrorist attack, as an employer, you are required by law to protect employees, customers, volunteers and other people visiting your sites from harm.
If you’re unfortunate enough to be part of an attack, you need to have a system in place to identify and manage the risks. This will help your organisation to keep people safe and give confidence to those working in or visiting your site by showing that you have taken measures to protect them. This will also reduce the adverse effects that might result from an attack, helping you to protect your reputation or brand and minimise financial losses.
This guidance provides information which will help you take forward a strong risk management system which will prepare your organisation to cope better if you should be caught up in an attack.
The sections below provide a broad overview of the ProtectUK Risk Management Process and Protect UK Approach, including its supporting resources.
The ‘related content’ page on ProtectUK’s Risk Assessment Process will take you through the ProtectUK Approach step-by-step.
ProtectUK Risk Management Process
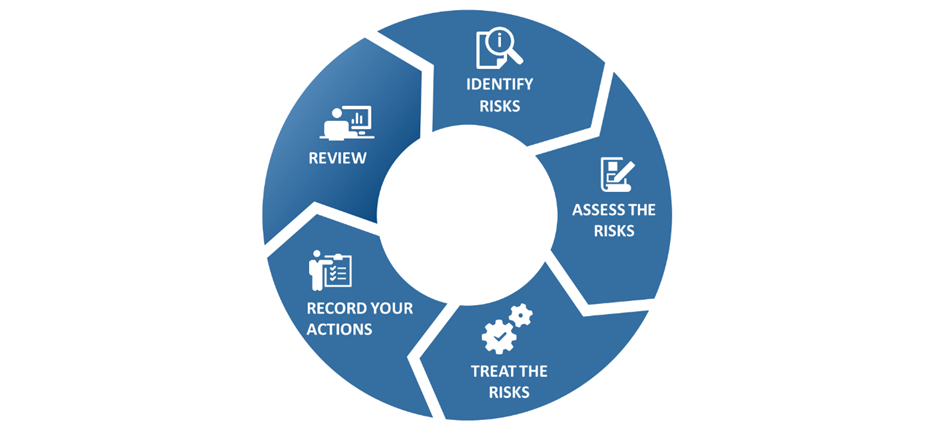
The ProtectUK Risk Management Process (RMP) has been tailored specifically to manage terrorist risk. It is adapted from the general risk management process found in a number of standards, including ISO/IEC 31000 and ISO/IEC 27005. The approach consists of five key stages that capture the following core activities:
- Stage 1: Identify the risks
- Stage 2: Assess the risks
- Stage 3: Treat the risks
- Stage 4: Record your actions
- Stage 5: Review
The above activities are supported by the ProtectUK risk assessment templates:
- ProtectUK Risk Identification Template
Supports Stage 1 of the ProtectUK Risk Assessment Process - ProtectUK Risk Assessment Template
Supports Stages 2-3 of the ProtectUK Risk Assessment Process
The process of recording and reviewing risks (Stages 4-5) are actively supported by the consistent use of these templates.
The ‘related content’ page on ProtectUK’s Risk Assessment process will take you through the ProtectUK Approach step-by-step.
ProtectUK Approach
The ProtectUK Approach forms the basis of the ProtectUK RMP guidance. It offers a pre-set approach to assessing terrorist risk that is intended to help familiarise you with how to undertake a risk assessment and how to effectively use the ProtectUK templates. This approach is presented step-by-step to provide you with one example of how a terrorist risk assessment might be undertaken.
While the ProtectUK Approach is freely available for use, its primary intention is to act as a broad example to all businesses. In order for you to gain the most value and insight from the risk management process, your risk assessment should be adapted to reflect what is important to your organisation. To support you in achieving this, additional information is provided across this guidance that will help you to understand core risk management concepts, techniques and approaches. This will assist you in tailoring your risk assessment to your organisation in the future.
ProtectUK Controls List
In risk management, a control is any measure or action that modifies risk. In order to address the risk of terrorism, you will need to introduce controls that modify the risk you face to an acceptable level for your organisation.
The ProtectUK Controls List has been designed specifically to help you achieve this. The list takes its inspiration from the operational level controls included in ISO/IEC 27001, and groups a number of broad counter-terrorism related controls across 12 distinct categories:
- Policies and Procedures
- Internal Organisation
- People and Personnel
- Access Control
- Physical Environment Security
- Cybersecurity
- Asset Security
- Service Delivery
- Communications
- Security Incident Preparedness and Response
- Security Incident Management
- Business Continuity
The ProtectUK Controls list may be used in conjunction with the enhanced controls captured within the Menu of Tactical Options (MoTO) to help manage terrorist risk.
Menu of Tactical Options (MoTO)
The Menu of Tactical Options provides a list of prescriptive, enhanced controls that should be considered to support your business when there has been an increase in threat level to critical, or following an incident or attack. These controls may be introduced alongside the controls listed in the ProtectUK Controls List to offer an enhanced response to potential terrorist threats. This may include stepping up the measures you already have in place, or introducing new controls temporarily.
The control measures outlined in MoTO are intended for implementation during times of increased risk and may be unsuitable or unsustainable for your organisation in the long-term. This is due to the increase in resource and financial commitment that these controls are likely to require. MoTO controls should therefore be subject to informed revision when the threat level decreases. This should be assessed and evaluated using the RMP.
